Deploying Multifactor Authentication (MFA)
EXECUTIVE SUMMARY
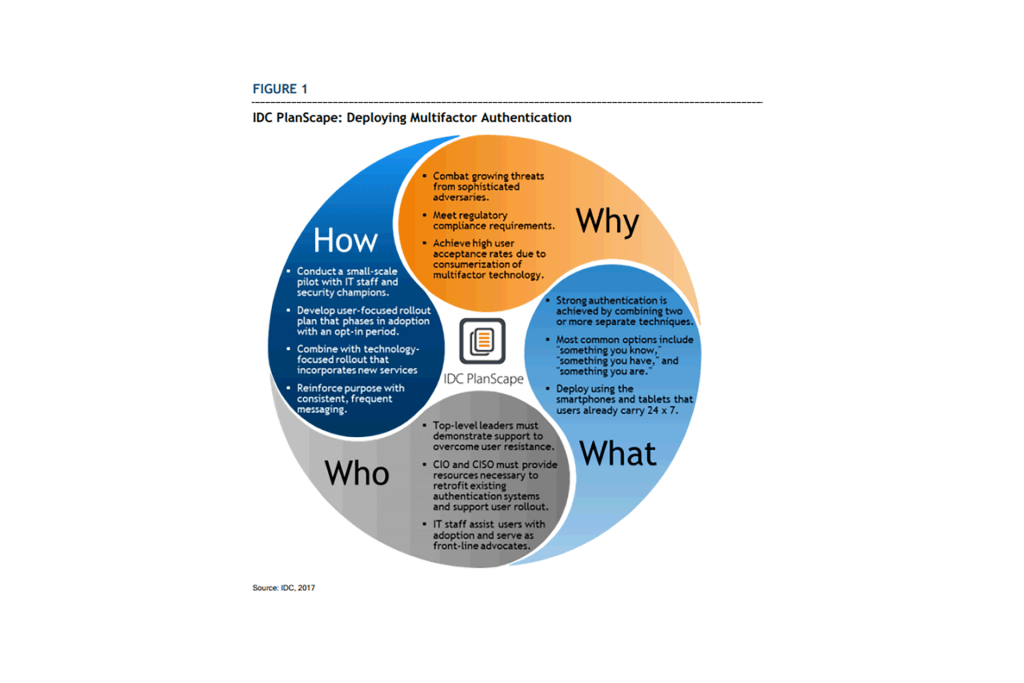
Multifactor authentication (MFA) provides organizations with an effective security control that overcomes the weaknesses of knowledge-based authentication and protects network, application, and data assets in an increasingly sophisticated threat environment. By combining passwords with physical devices and/or biometric measurements, organizations add a layer of strong security and protect themselves against password theft.
Recent advances in multifactor authentication make this technology more accessible to nontechnical end users and allow widespread deployment throughout the organization. Using multifactor authentication may now be as simple as clicking a button on a pop-up window that appears on the smartphone that a user was already carrying. The simplicity of this approach improves security while increasing user satisfaction.
Organizations planning the deployment of multifactor authentication should consider approaching both users and services in a phased approach that prioritizes high-risk users and applications to achieve the greatest benefit as early as possible in the deployment. Communicating frequently with both management and end-users increases the likelihood of a smooth deployment.
WHY IS MULTIFACTOR AUTHENTICATION IMPORTANT?
Organizations that rely solely upon passwords for authentication are taking a significant risk in today’s cybersecurity threat environment. While passwords remain a useful component of any organization’s security program, they now fall into the category of “necessary, but not sufficient” as a means of proving user identity. Multifactor authentication approaches, long the realm of classified government agencies, financial institutions, and others with security postures bordering on paranoia are now a critical component of even the most routine technology services.
Data gathered from recent security incidents bears out this claim. In its “2017 Data Breach Investigations Report,” Verizon examined the details of thousands of security incidents that took place in 2016. “81% of confirmed data breaches involved weak, default or stolen passwords,” underscoring the fact that password authentication can simply no longer stand on its own for more than the most inconsequential of services. There is a high likelihood that any service that runs at scale and reliesonly upon password authentication is already compromised by adversaries if the service offers information or resources of any value.
This IDC study provides senior technology leaders with a multifaceted approach to multifactor authentication.
[pdf-embedder url=”https://www.xbandenterprises.com/uploads/2020/03/Deploying_Multifactor_Authentication-1.pdf” title=”Deploying Multifactor Authentication MFA”]